Dec 24, 2025Ravie LakshmananOnline Fraud / Artificial Intelligence
The fraudulent investment scheme known as Nomani has seen a significant increase of 62%, as reported by the Slovak cybersecurity company, ESET. This surge comes as campaigns promoting the scam have expanded from Facebook to platforms like YouTube.
ESET indicated that it blocked over 64,000 unique URLs associated with the Nomani scheme this year, with the majority of detections originating from countries including Czechia, Japan, Slovakia, Spain, and Poland. First documented in December 2024, Nomani employs social media malvertising, company-branded posts, and AI-generated video testimonials to lure users into investing in non-existent products promising high returns.
Victims who seek payouts are often prompted to pay additional fees or provide personal information, such as identification and credit card details. The overarching objective of this type of investment scam remains financial loss for the victims.

Compounding the issue, fraudsters also exploit Europol and INTERPOL-related lures on social media, promising assistance in recovering stolen funds, which often leads to further financial loss for victims. ESET reported that the scam has evolved, with improvements making AI-generated videos appear more realistic, thereby complicating the identification of the deception.
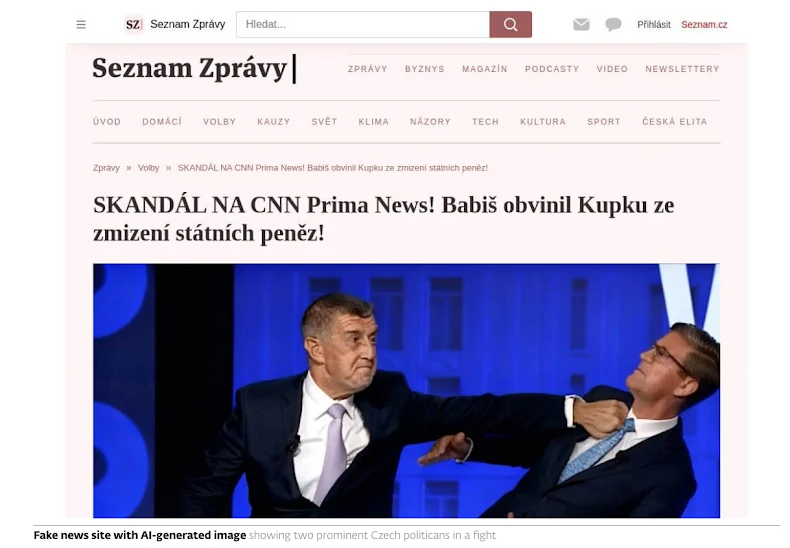
“Deepfakes of popular personalities, used as initial hooks for phishing forms or websites, now use higher resolution, have significantly reduced unnatural movements and breathing, and have also improved their A/V sync,” ESET noted. This fabricated content frequently leverages topical events or widely recognized figures to enhance credibility. For instance, in one observed case in Czechia, a fake news article falsely claimed government investment through a scam cryptocurrency platform.
To evade detection, the fraudsters limit the duration of their campaigns to just a few hours and utilize benign cloaking pages to redirect users when targeting criteria are not met. “To further lower their footprint, attackers increasingly abuse legitimate tools offered by the social media ad framework, such as forms and surveys instead of external webpages, to harvest victims’ information,” ESET explained.
Improvements in phishing page templates suggest the use of AI tools to generate HTML code, evidenced by checkboxes found in the source code comments. The investigation pointed to GitHub repositories hosting such templates being associated with users from Russia and Ukraine.

Despite the enhancements to the Nomani scheme, ESET reported a decline in detections during the second half of 2025, suggesting that law enforcement efforts are pressuring the attackers to change their tactics. “On the bright side, although overall detections are up compared to 2024, there’s a hint of improvement, as H2 2025 detections have declined by 37% compared to H1 2025,” the company stated.
This report coincides with a recent investigation by Reuters, which revealed that 19% of Meta’s $18 billion in ad sales in China last year stemmed from ads for scams, illegal gambling, pornography, and other prohibited content run by the company’s ad agency partners. Following this revelation, Meta is reportedly reviewing the program. It was also reported that the company anticipates earning 10% of its global revenue for 2024—approximately $16 billion—from such ads, highlighting the immense scale of the issue.
See also Shadow AI Poses Security Risks for SaaS Integrations, Warns Nudge Security CTO
Shadow AI Poses Security Risks for SaaS Integrations, Warns Nudge Security CTO AI-Powered Cybersecurity Solutions Achieve 95% Detection Accuracy in Real-Time Threats
AI-Powered Cybersecurity Solutions Achieve 95% Detection Accuracy in Real-Time Threats AI-Driven Cyberattacks Surge: Manufacturers Must Patch Vulnerabilities Before 2026
AI-Driven Cyberattacks Surge: Manufacturers Must Patch Vulnerabilities Before 2026 Tenable Reveals 2026 Cybersecurity Predictions: AI-Driven Attacks and Custom Security Tools
Tenable Reveals 2026 Cybersecurity Predictions: AI-Driven Attacks and Custom Security Tools Boards in 2026 Prioritize Cybersecurity and Diversity for Future-Proof Governance
Boards in 2026 Prioritize Cybersecurity and Diversity for Future-Proof Governance







































































