As businesses grapple with the evolving landscape of cybersecurity, a new arms race has emerged, pitting organizations against increasingly sophisticated cybercriminals who are leveraging advancements in artificial intelligence (AI). In this environment, generative AI, synthetic identities, and deepfake technology are becoming tools for attackers, enhancing their capacity to execute aggressive phishing attacks. Concurrently, security teams are under pressure to automate detection mechanisms, refine response strategies, and integrate AI into their defensive frameworks.
The stakes are high; according to IDC’s FutureScape 2026 predictions, by 2027, a staggering 80% of organizations will face phishing attacks stemming from synthetic identities that combine real personal data with AI-generated content, creating alarmingly convincing digital personas. This shift signifies a structural change in the threat landscape, challenging conventional security protocols.
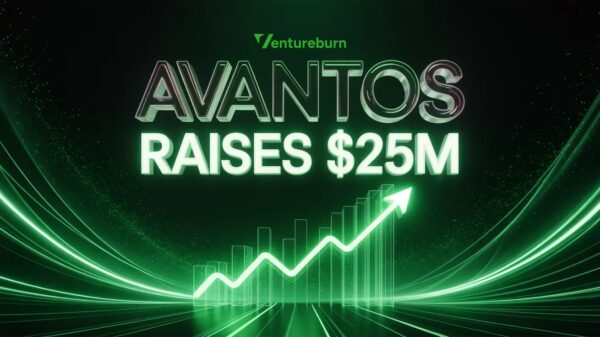
A notable instance underscoring this trend involved a cybercriminal utilizing AI-generated replicas of high-ranking executives to orchestrate a $25 million fraudulent transfer. Grace Trinidad, a prominent analyst in the field, noted that organizations now require a “safe word” to authenticate transactions, ensuring they are not manipulated by fraudulent actors masquerading as executives. The capacity for AI to facilitate impersonation has outpaced traditional trust frameworks, necessitating their rapid evolution.
Central to tackling these threats is the quality of data feeding into AI-driven security systems. High-quality telemetry is crucial, as highlighted by Trinidad, who stated, “When you have very high-quality telemetry, that naturally cascades into good AI output.” This assertion aligns with IDC’s broader guidance suggesting that organizations failing to prioritize robust, AI-ready data will suffer a 15% productivity loss by 2027, highlighting the critical nature of data integrity in cybersecurity.
As the threat landscape shifts, traditional breach response playbooks—which tend to be static and manually updated—are becoming obsolete. The future lies in dynamic, real-time adaptation. Trinidad predicts a shift towards personalized breach response, with organizations employing telemetry from their environments to create tailored playbooks. By 2030, it is anticipated that 45% of organizations will centrally manage the orchestration of AI agents to enhance collaboration and ensure ethical governance of AI deployments, making security a priority in this transformation.
However, as organizations explore these technological advancements, the integration of AI raises concerns about governance. Many firms are still in the experimental phase, lacking a cohesive strategy for enterprise-wide AI deployment. Trinidad remarked, “We’re not quite there yet… I don’t know any organization that I would say they’re a standout example of AI integrated throughout the enterprise.” Without appropriate governance, AI risks becoming a new vector for attacks.
Looking ahead, IDC forecasts that by 2028, all Global 100 companies and half of the Global 1000 will invest at least $2 million annually in unified AI governance software, emphasizing security, ethics, and privacy. Governance should not be seen as a hindrance to innovation but rather as a necessary framework for safe scalability.
In light of these developments, Chief Information Security Officers (CISOs) and Chief Information Officers (CIOs) are advised to take decisive action. Key steps include auditing data foundations, enhancing detection controls for synthetic identities, modernizing breach response strategies, investing in AI governance frameworks, and establishing metrics that accurately assess human-AI collaboration rather than merely automation efficiency.
As organizations navigate this new landscape, the question arises: Who will ultimately benefit from AI—defenders or attackers? Trinidad emphasizes that the battle is a zero-sum game, remarking, “As the ways that we protect ourselves become more dynamic and more responsive and more agile, threat actors are also going to up their game.” The true differentiator will not be the speed of AI adoption but rather the strategic integration of AI across data management, workforce collaboration, governance, and operational orchestration. Facing powerful crosscurrents, including geopolitical uncertainties and regulatory shifts, organizations that adopt a deliberate strategy can transform these challenges into competitive advantages.
For further insights on how agentic AI is set to reshape cybersecurity and enterprise operations in the coming years, readers are encouraged to explore IDC’s FutureScape 2026 predictions and Grace Trinidad’s comprehensive interview in BizTech Magazine.
See also Anthropic’s Claims of AI-Driven Cyberattacks Raise Industry Skepticism
Anthropic’s Claims of AI-Driven Cyberattacks Raise Industry Skepticism Anthropic Reports AI-Driven Cyberattack Linked to Chinese Espionage
Anthropic Reports AI-Driven Cyberattack Linked to Chinese Espionage Quantum Computing Threatens Current Cryptography, Experts Seek Solutions
Quantum Computing Threatens Current Cryptography, Experts Seek Solutions Anthropic’s Claude AI exploited in significant cyber-espionage operation
Anthropic’s Claude AI exploited in significant cyber-espionage operation AI Poisoning Attacks Surge 40%: Businesses Face Growing Cybersecurity Risks
AI Poisoning Attacks Surge 40%: Businesses Face Growing Cybersecurity Risks