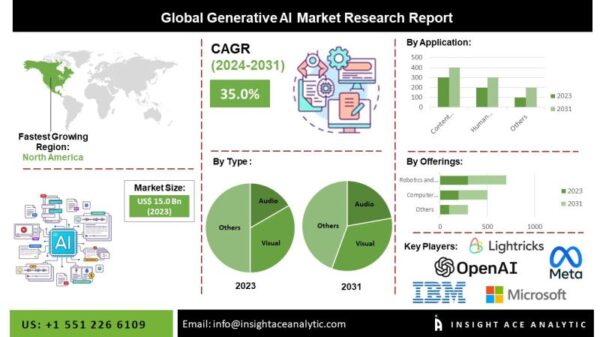
Threat actors are now operating at unprecedented speeds, leveraging artificial intelligence (AI) and automated tools to enhance the effectiveness and scope of cyberattacks. This evolution in tactics significantly strains traditional defense mechanisms, as organizations struggle to keep pace with the rapidity and volume of these incursions.
In an interview with Information Security Media Group, Jas Sood, president of strategics west and U.S. healthcare at Palo Alto Networks, and Sam Rubin, senior vice president of consulting and threat intelligence at Unit 42, Palo Alto Networks, discussed the challenges facing cybersecurity professionals. They highlighted that the complexity of modern digital environments often hampers defense efforts. Organizations typically deploy a multitude of security tools, each generating disparate data that seldom aligns with one another. This misalignment leaves cybersecurity analysts grappling with logs and telemetry that are not actionable in a timely manner, ultimately obscuring early warning signals and delaying response and containment.
Sood and Rubin emphasized that the phenomenon of “tool sprawl” complicates detection efforts, as the inefficiencies in managing numerous security solutions can create significant gaps in visibility. The duo pointed out that while organizations invest heavily in security technologies, the lack of integration among these tools reduces overall effectiveness.
AI technologies, however, present a potential solution to these data management problems by correlating events across different systems, thereby enhancing situational awareness. This capability allows security teams to respond more swiftly and effectively to threats, addressing a critical gap in current cybersecurity frameworks. They noted that the integration of AI not only assists in data correlation but also enables predictive analytics that can identify patterns and anomalies indicative of cyber threats.
In today’s threat landscape, identity management remains a prominent vulnerability, serving as the most common entry point for attackers. Rubin and Sood underscored the need for organizations to bolster their identity verification processes to mitigate this risk. As adversaries increasingly exploit identity weaknesses, companies must prioritize robust authentication mechanisms to strengthen their defenses.
The conversation also touched on the broader implications of these evolving cyber threats. With AI enhancing the capabilities of attackers, the urgency for organizations to adapt their security strategies becomes more pronounced. The ability to harness AI effectively could define the next frontier in cybersecurity, as companies strive to create resilient defenses capable of withstanding rapid, sophisticated attacks. As these technologies continue to advance, the cybersecurity landscape stands at a crossroads where proactive measures and innovative solutions will be essential for safeguarding sensitive data and maintaining operational integrity.
See also Anthropic’s Claims of AI-Driven Cyberattacks Raise Industry Skepticism
Anthropic’s Claims of AI-Driven Cyberattacks Raise Industry Skepticism Anthropic Reports AI-Driven Cyberattack Linked to Chinese Espionage
Anthropic Reports AI-Driven Cyberattack Linked to Chinese Espionage Quantum Computing Threatens Current Cryptography, Experts Seek Solutions
Quantum Computing Threatens Current Cryptography, Experts Seek Solutions Anthropic’s Claude AI exploited in significant cyber-espionage operation
Anthropic’s Claude AI exploited in significant cyber-espionage operation AI Poisoning Attacks Surge 40%: Businesses Face Growing Cybersecurity Risks
AI Poisoning Attacks Surge 40%: Businesses Face Growing Cybersecurity Risks